Many organisations rely on 802.1X to secure office networks. It authenticates devices before they connect and enforces strong access control. In a traditional office environment where IT…
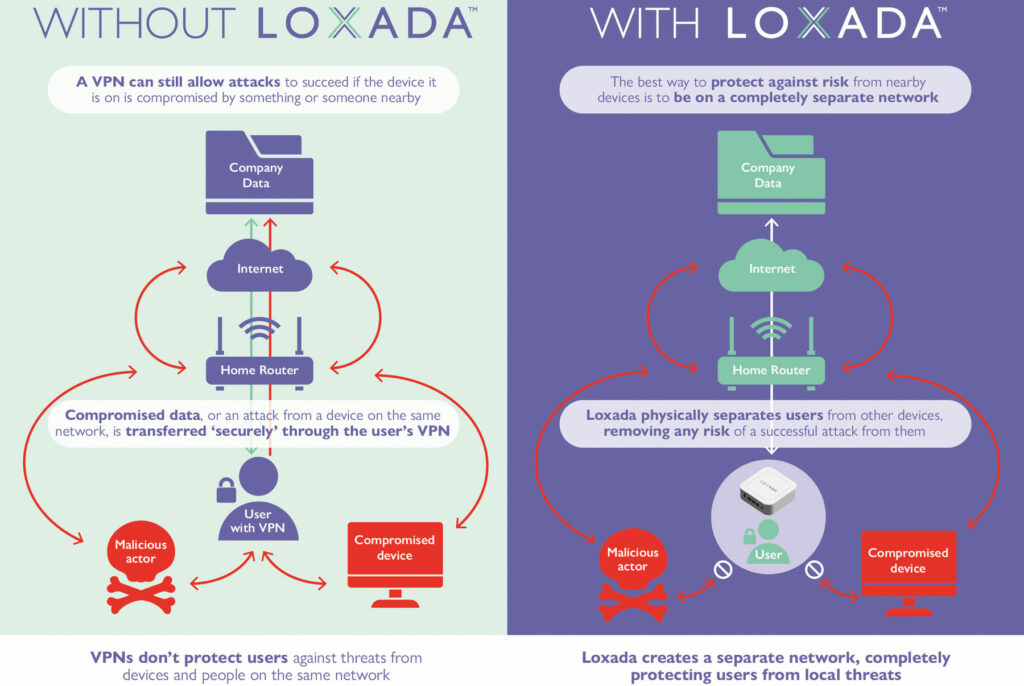
When people talk about cybersecurity, two terms often come up: VPN and firewall. Both are important, but they are not the same. A VPN, or…

In today’s cybersecurity landscape, traditional defences alone are no longer enough. Zero Trust has become a key strategy for protecting sensitive systems. It starts from…

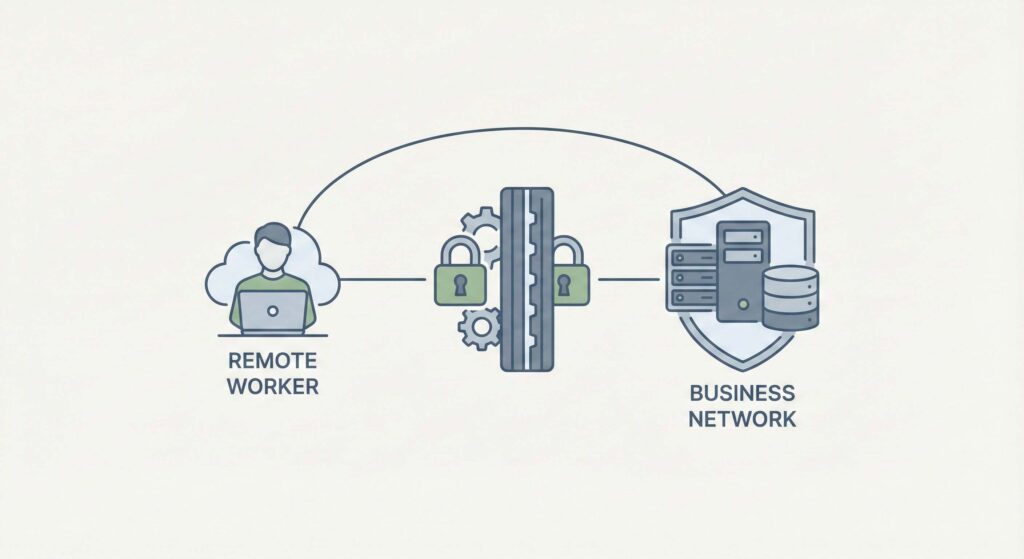
The way people access company systems has changed. Even organisations that encourage staff to work from the office still have people logging in from home…
How to Protect Your Wi-Fi Login Details When Working From Home When working from home, your Wi-Fi login credentials become a critical security element. The…

Cyber Security Checklist for Remote Workers As more professionals access sensitive data from locations outside office IT infrastructure, maintaining strong cybersecurity is essential. Whether you…