When people talk about cybersecurity, two terms often come up: VPN and firewall. Both are important, but they are not the same.
A VPN, or Virtual Private Network, creates a private tunnel for data to travel across the internet. A firewall acts like a barrier, filtering the traffic that flows into and out of a system.
At first glance, it may seem like choosing one or the other would be enough. In reality, businesses need both. They also need to consider how these tools work when staff connect from the uncontrolled network edge, such as homes, hotels, serviced offices, and client sites. These are environments that IT teams cannot govern directly, yet they are now part of the daily reality of how staff access company systems.
What a VPN Does
A VPN secures data in transit. It encrypts the information moving between a device and the company’s systems, which helps prevent outsiders from listening in. This matters when people are using public or shared connections.
Picture a member of staff logging into a company dashboard from a hotel room or pulling up sensitive files from the kitchen table at home. Without a VPN, that traffic could be visible to others on the same network. With a VPN in place, the data is scrambled and hidden from view.
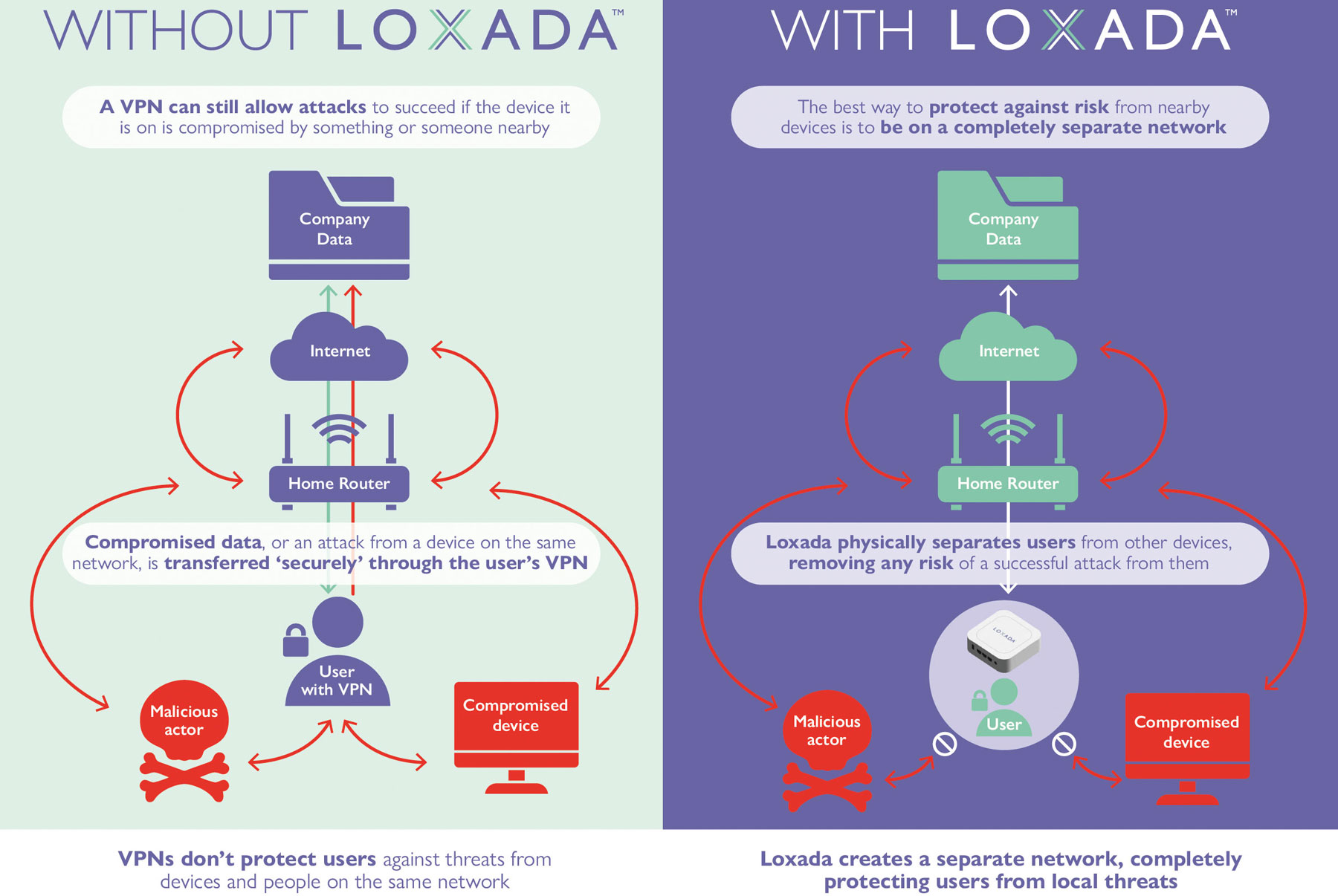
But a VPN only solves part of the problem. It does not prevent a compromised smart TV, guest phone, or gaming laptop on the same home network from trying to move laterally into the company system once the connection is made. At the uncontrolled network edge, where IT has no authority over the router or the devices connected to it, a VPN is not enough to stop this type of threat.
What a Firewall Does
A firewall is different. Instead of encrypting traffic, it filters it. Firewalls decide which connections to allow and which to block, based on rules and policies. They can prevent harmful files from entering a network or block suspicious outgoing requests.
This is powerful in an office environment where IT controls the network. But when someone connects from a serviced office or client site, the firewall has to sit behind a router that may not have been patched or secured in years. That weak link can let attackers in before the firewall even sees the traffic.
Firewalls are an important part of the puzzle, but like VPNs, they do not close the security gaps created at the uncontrolled network edge.
Why One is Not Enough
It is tempting to think of a VPN as “security” or a firewall as “protection” and stop there. But each has clear limits.
- A VPN keeps data private while it is moving, but it does not filter harmful content once it arrives.
- A firewall filters traffic, but it does not guarantee that the traffic is encrypted while crossing untrusted networks.
The two are complementary. A useful way to think about it is travel. The VPN is the vehicle that hides you on the road. The firewall is the checkpoint that inspects what you bring with you when you arrive. Neither can replace the other.
And yet, even when both are in place, there is still a weak spot if staff are connecting from networks IT does not control.
Why the Uncontrolled Network Edge is a Blind Spot
The uncontrolled network edge has become one of the biggest blind spots in business security. It is where staff connect to work systems from places such as homes, hotels, serviced offices, or client sites.
The routers in these environments may be outdated or insecure. They may never receive firmware updates. They may also be shared by many devices, from children’s laptops to visiting guests’ phones, any of which could already be compromised.
Real-world examples make this clear:
- A finance manager downloads reports from home while their teenager streams games on the same Wi-Fi. If the teenager’s device carries malware, the company system is suddenly exposed.
- A solicitor accesses a case management system from a serviced office where the shared router has not been updated in years. Attackers scanning the internet for weak routers can slip in and ride the same connection.
- A consultant logs into client dashboards from the client’s own office network. The company has no visibility into how that network is secured, but their systems are still being accessed through it.
In all of these cases, VPNs and firewalls help but cannot remove the underlying risk. The uncontrolled network edge remains the weak point.
The Role of a Secure On-Ramp
This is where the idea of a secure on-ramp becomes essential. Instead of leaving staff to depend on whatever router or Wi-Fi they happen to be using, organisations can provide them with a secure, dedicated way of connecting back into company systems.
At Loxada, we do this through managed routers with hardened firmware. These create a separate, work-only environment at the uncontrolled edge, so business traffic is kept apart from other devices. All activity is encrypted, inspected, and updated automatically.
Because the routers are centrally managed, IT teams retain visibility and control, even when staff are working from places that would otherwise be outside their reach. Staff do not need to install software or manage settings. They simply plug in and connect safely.
The secure on-ramp turns unmanaged environments such as homes or hotels into safe access points, giving businesses confidence that sensitive systems are not exposed to avoidable risks.
Why This Matters
Cyber attackers know that the uncontrolled network edge is often the easiest way into a company system. Many home and small-office routers are outdated. Many hotel and shared office networks are not patched quickly. Attackers can exploit these weaknesses to bypass strong security controls inside the company itself.
Agencies such as the NSA, GCHQ, and CISA have all warned about these risks and advised businesses to secure the edge using centrally managed solutions. Ignoring this guidance leaves organisations open to breaches that start outside their controlled perimeter.
By combining VPNs, firewalls, and a secure on-ramp at the uncontrolled network edge, businesses can reduce their attack surface, protect sensitive systems, and maintain compliance with frameworks such as GDPR, PCI DSS, and NIS2.
The Bottom Line
A VPN is not the same as a firewall. Each plays a different role, and both are needed. But neither one is enough on its own, particularly when staff are connecting from uncontrolled environments such as homes, hotels, serviced offices, or client sites.
To close the gap, organisations need to focus on the uncontrolled network edge and provide a secure on-ramp that ensures staff can reach company systems safely, wherever they are.
With Loxada’s managed routers, this becomes straightforward. Staff get safe, reliable access, while IT keeps control of visibility, security, and compliance.
It is a simple way to eliminate one of the biggest blind spots in modern security and to protect business systems in a world where access is no longer limited to the office.