
Law Enforcement
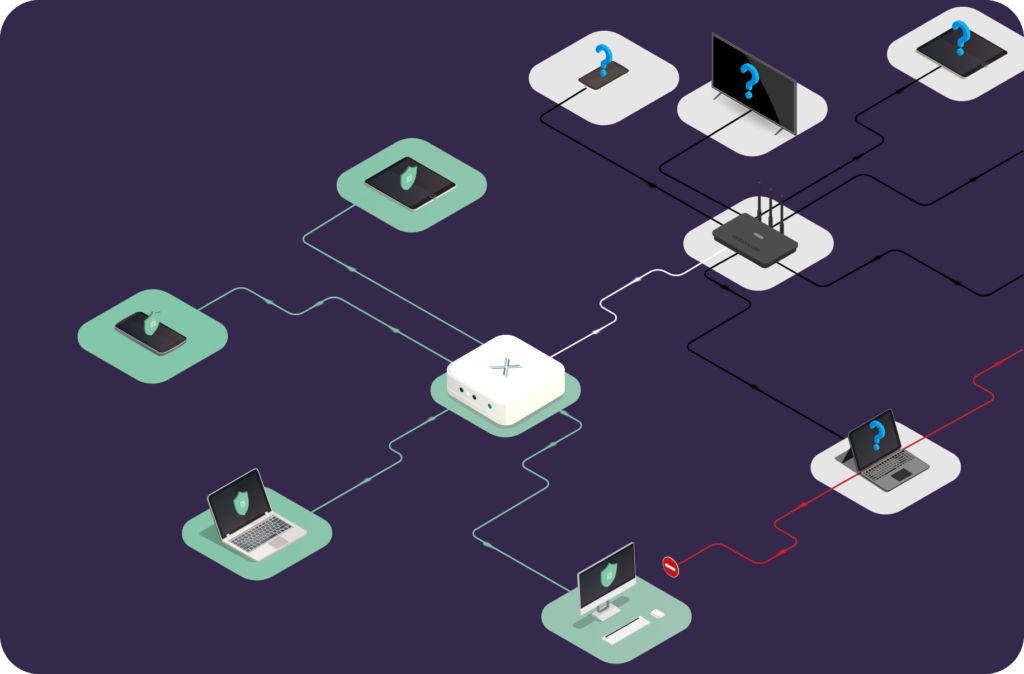
Law enforcement officers now access sensitive case systems from various locations beyond the office, making uncontrolled networks an increasing risk.
This is the uncontrolled network edge, one of today’s primary risk zones for law enforcement. Whether the threat is a foreign-manufactured router, unpatched consumer hardware, or simple human error, local and regional departments urgently need a way to protect data while avoiding added complexity.
Loxada helps police departments and sheriff’s offices secure remote access to sensitive systems, even when staff are connecting from home, vehicles, or partner sites. Our managed routers establish a trusted, auditable connection point, aligned with CJIS security requirements and best practices from the NSA and CISA.
Small Departments Face Big Threats
Cybercrime has changed. Hacking tools that once required years of training are now widely available through:
- Hacking-as-a-Service marketplaces
- AI-assisted attack tools
- Pre-packaged scripts for router scanning and exploitation
- Public databases of unpatched or default-configured routers
Law enforcement agencies, especially smaller ones, are now in the crosshairs targeted both directly (to access case systems) and indirectly (via shared networks or exposed devices).
And it’s not just hackers.
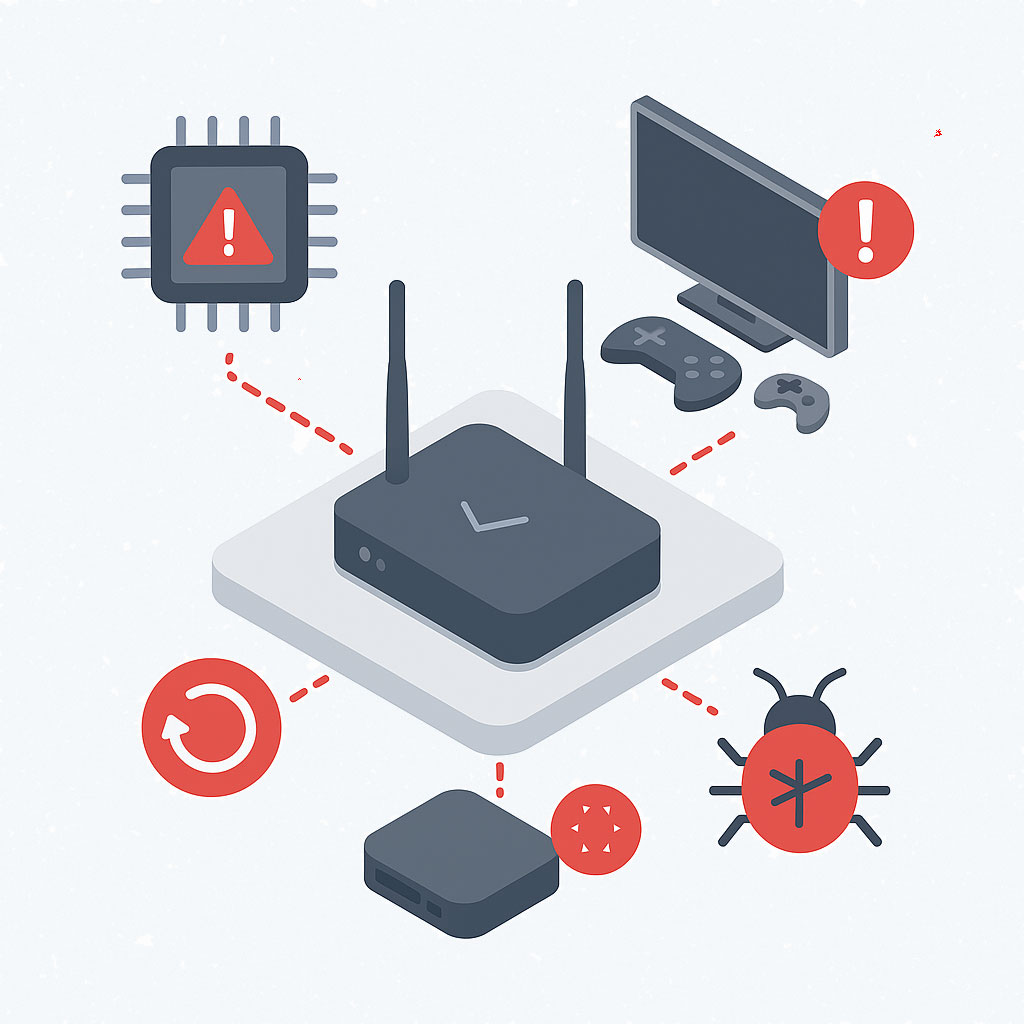
Misconfigured home routers, unverified firmware, and poorly maintained ISP hardware can create silent vulnerabilities that breach CJIS standards.


Common Risk Scenarios We See
Smaller departments are often under-resourced and rely on ad hoc IT support or older infrastructure. Some examples:
- A detective reviewing reports from home over a family Wi-Fi network
- An officer uploading bodycam footage using hotel or coffee shop Wi-Fi while traveling for training
- A clerk entering arrest data from a shared admin PC on a third-party network
- Investigators working part-time across precincts or partner agencies
- Shared routers in temporary precinct buildings or mobile command vehicles
Each of these situations increases the likelihood of a network-based compromise, even if endpoints are fully protected.
Why VPNs Aren’t Enough
VPNs are a common tool in law enforcement, but departments cannot rely solely on them.
VPNs encrypt traffic, but they don’t:
- Protect against compromised routers or firmware backdoors
- Prevent malicious traffic on the same network
- Ensure that the router itself hasn’t been tampered with
- Stop lateral movement from other devices sharing the network
Loxada works with existing VPNs by controlling network entry, ensuring remote access always starts from a secure, known-good state, a key CJIS Security Policy requirement.

Built for CJIS Compliance, Without the Overhead
Meeting CJIS standards can be difficult for smaller forces. Loxada helps address several core requirements:
5.5 – Remote Access
Requires encrypted connections, device validation, and network controls.
Loxada routers use an always-on VPN tunnel with tamper-proof firmware.
5.10 – System Integrity
Mandates control of firmware, configuration, and update processes.
Loxada’s proprietary firmware is designed for security auto-updates with signed builds.
5.13 – Wireless Access Control
Demands secure, authorised wireless networks.
Loxada creates a centrally managed, encrypted Wi-Fi network, completely separate from local traffic.
All updates are deployed automatically, ensuring departments stay secure, even without dedicated IT teams.
How It Works
Loxada routers are shipped pre-configured and ready to go. Setup takes just minutes:
- Officers plug in the device at home, in the field, or on location
- A secure, dedicated work network is created instantly
- All traffic is routed via Loxada’s encrypted tunnel
- Devices stay isolated from local networks and consumer routers
- No technical expertise is needed, no setup, no updates, no management burden
If access is revoked (e.g. staff leave), the device resets to a secure state and can be reassigned.


Why This Matters for Law Enforcement
Why This Matters for Law Enforcement:
- Many devices ship with unpatched firmware and exploitable defaults
- Even factory resets often don’t remove backdoors
- Supply chain compromises and unknown vendor firmware raise red flags under CJIS
- Public Wi-Fi networks remain a serious exposure point for officer devices
Loxada removes this ambiguity. We give departments full control over the network edge, not just the applications and data.
Why Local Law Enforcement Agencies Choose Loxada
- Protects CJIS access from home, vehicle, or shared locations
- Blocks lateral attacks from unsecured networks
- Simplifies compliance with CJIS, NSA, and CISA recommendations
- Eliminates firmware risk with custom-managed updates
- Requires no IT overhead, ideal for under-resourced departments
- Works alongside existing VPNs and security controls