
Defense
Defense contractors operate in a complex, high-stakes environment. Whether supporting classified programs, working under ITAR restrictions, or maintaining critical infrastructure contracts, your systems must uphold the highest standards of security, even outside your primary facilities.
From engineers accessing secure documentation at home to technicians working on-site at partner locations, today’s defense supply chain depends on connectivity that’s often beyond direct IT control.
This is the uncontrolled network edge, the point where your defenses end and external risks begin.
This vulnerability is now one of the most prevalent weaknesses in modern cybersecurity.
Loxada provides a secure, managed network edge, purpose-built for places where supply chain trust, firmware transparency, and connectivity integrity are essential.
The Evolving Threat: Hacking as a Commodity
Defense suppliers now face a professionalized threat ecosystem. Hacking-as-a-Service and AI-powered attack automation make it easier than ever for adversaries to scale their operations.
This shift means:
Attackers can buy access to compromised infrastructure on the dark web
AI tools can automate phishing, scan for vulnerabilities, or spoof networks
Low-skill actors can deploy exploits written by others, with minimal expertise
Home or third-party routers become high-value targets for surveillance or disruption
Even with secure systems and well-trained personnel, a compromised network can put everything at risk. Your organization’s known network edge is no longer your true perimeter.

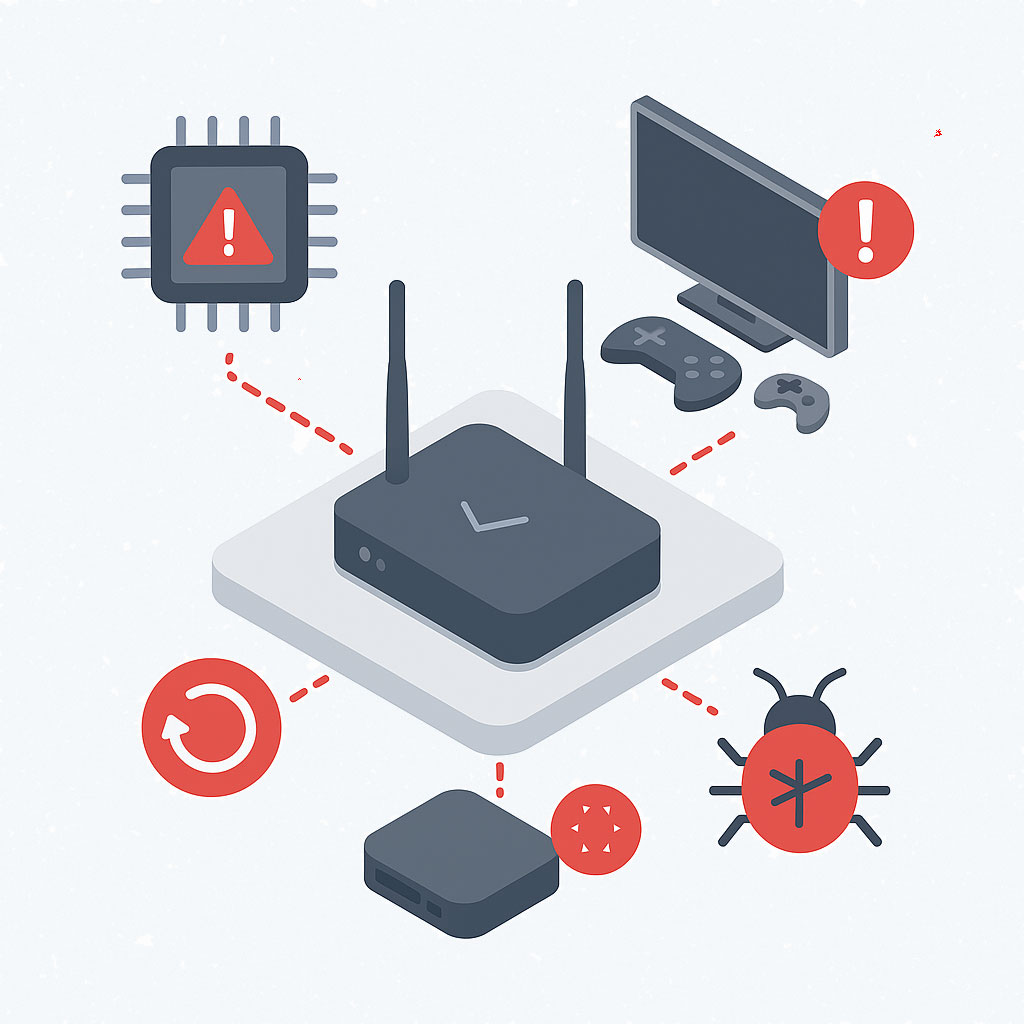
Why Network Integrity Matters to Defense Suppliers
Off-the-shelf and ISP-supplied routers and access points often fail to meet the compliance and operational demands of defense work.
Yet, many suppliers still use consumer-grade or unmanaged devices at remote locations, home offices, or during mobile deployments.
These devices can:
- Include undocumented services or vendor-specific remote access
- Contain unvetted third-party firmware components that may never be updated
- Allow factory resets that revert devices to insecure default states
- Accept software updates from unknown sources, without auditability
For companies involved in sensitive or restricted programs, this is more than a technical concern, it can jeopardize contracts, violate export controls, or expose data to adversarial actors.
Multiple US and allied agencies, including the NSA, CISA, and NCSC, have published formal guidance warning that routers and edge devices are now primary targets for cyberattacks.
The NSA’s 2025 recommendations emphasize the importance of securing network edge infrastructure and maintaining firmware-level integrity across your entire environment.
Loxada: A Known-Good Network Edge
Loxada offers hardened, managed routers that establish trust even where you don’t control the infrastructure. We replace original firmware entirely with Loxada’s security-focused OS, eliminating hidden services, backdoors, and unknown code paths.
Key features include:
- Loxada’s proprietary secure firmware
- Always-on VPN to a trusted gateway
- Automatic, verifiable updates from centrally controlled servers
- Rollback prevention to stop resets from returning to insecure states
- DNS-based threat blocking to protect against known malicious domains
No setup, user maintenance, or onsite IT is needed. Devices are ready to deploy out of the box.

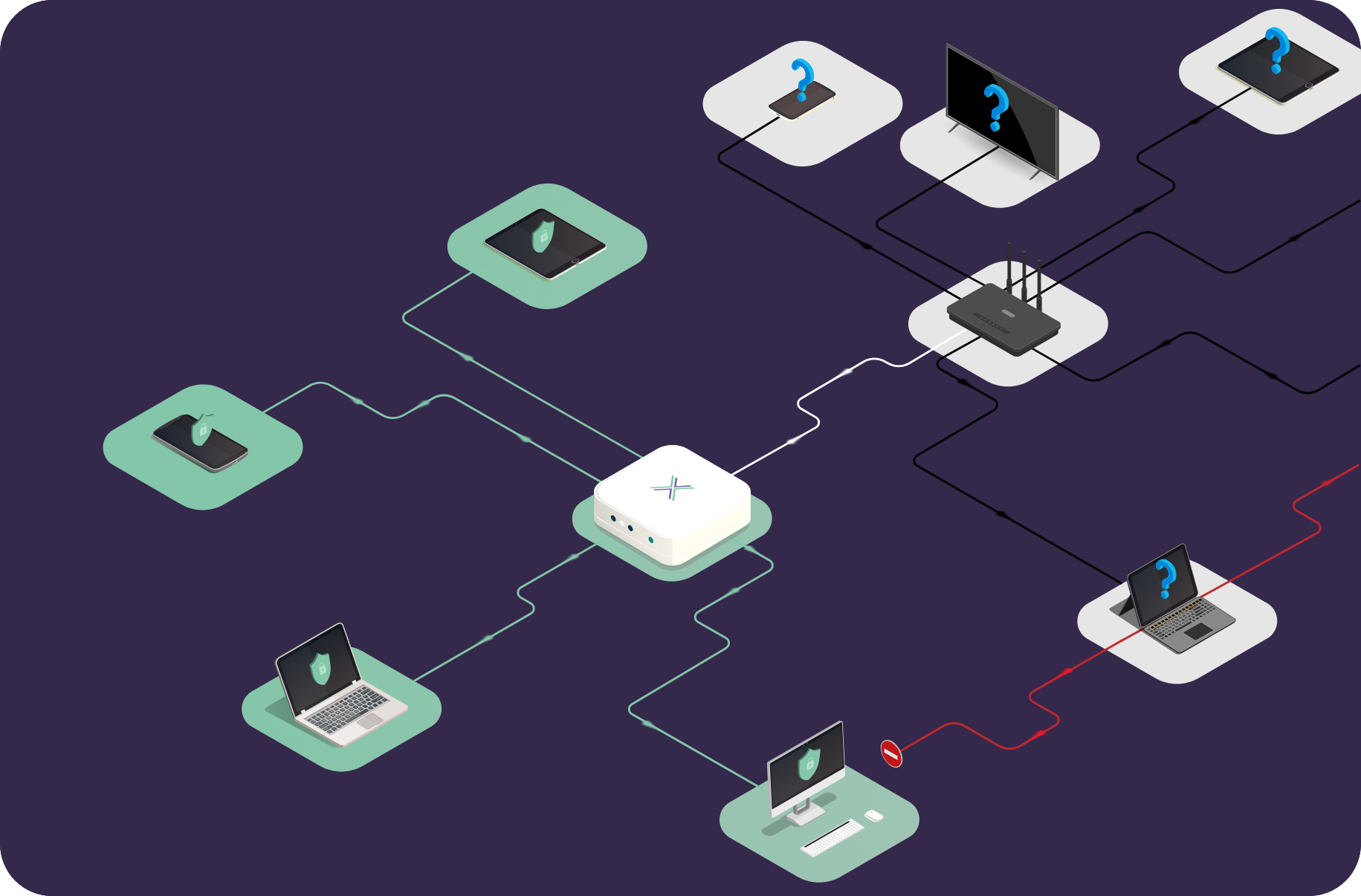
What Loxada Offers
Loxada provides your team with secure, trusted access to sensitive systems and data, regardless of their location.
Our managed routers:
- Replace manufacturer’s firmware with custom-built Loxada firmware
- Maintain an always-on VPN connection back to your firm’s infrastructure
- Block malicious domains and detect known bad traffic
- Auto-update securely, ensuring routers are always fully patched
- Prevent rollback to insecure states, even after a factory reset
No configuration required. No training needed. Just plug in, power up, and your connection is protected.
Flexible Deployment for Critical Teams
Loxada’s routers suit real-world defense needs, where flexibility counts and the network perimeter isn’t always yours to control.
Example use cases include:
- Home offices for engineers or compliance leads working on restricted programs
- Partner or subcontractor facilities where shared IT infrastructure is in use
- Field operations, including temporary deployments and live test sites
- Remote labs or pop-up engineering centers
- Small teams or mobile staff with no local IT resources
In all scenarios, Loxada helps extend your security perimeter to wherever secure work takes place ,without sacrificing control, compliance, or performance.


Why Defense Suppliers Choose Loxada
- Secures sensitive access across distributed teams and facilities
- Reduces risk at the network edge, where visibility is lowest
- Simplifies compliance for NIST 800-171, DFARS, and CMMC frameworks
- Aligns with NSA and CISA guidance on firmware and edge device security
- Deploys quickly, with no specialized hardware or configuration needed
Loxada gives your organization a clear and auditable way to protect sensitive connectivity, without introducing unnecessary complexity.