
Retailers
Retail cybersecurity typically protects customer-facing points, such as card readers and e-commerce platforms. These are rightly prioritised by IT teams.
But every transaction depends on systems beyond the till. Key logistics, finance, and HR teams often work outside IT’s direct control.
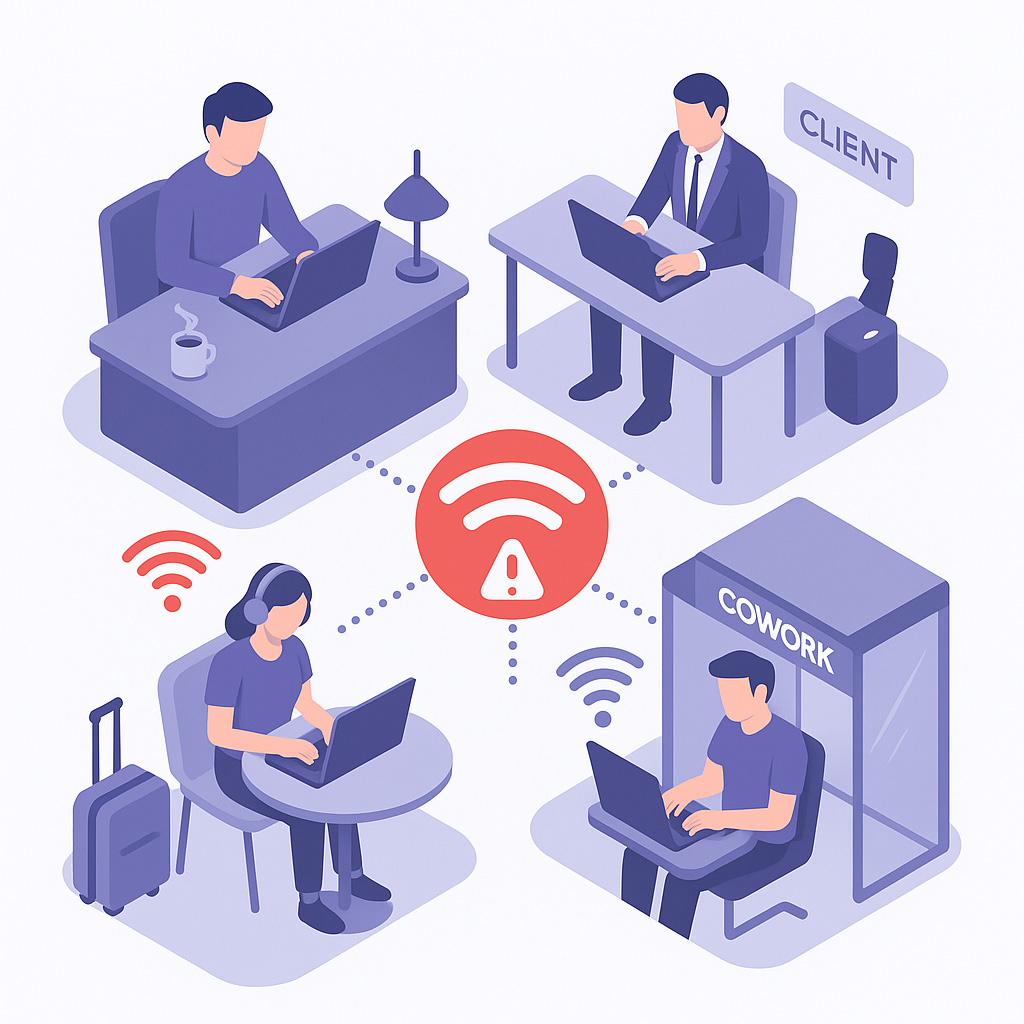
Whether it’s a regional manager working from home, a buyer connecting over airport Wi-Fi, or a warehouse supervisor reviewing reports in a leased facility, the risk emerges at the point of connection, the uncontrolled network edge.
This is where attackers increasingly look to compromise retail operations.
Modern Retail Means a Wider Attack Surface
The way retailers work has changed. Many core functions now take place across distributed teams, hybrid setups, and temporary locations. That brings flexibility, but it also introduces overlooked vulnerabilities:
- Head office or back-office staff accessing systems from home
- Supply chain partners using their own connectivity to interact with central systems
- Regional teams logging into portals from serviced offices or hotels
- Contractors connecting via untrusted networks to access finance or payroll tools
These access points often rely on off-the-shelf routers, many of which are poorly maintained, insecure by design, or invisible to your IT team. They can become the path of least resistance for attackers, especially when targeting backend systems critical to continuity.
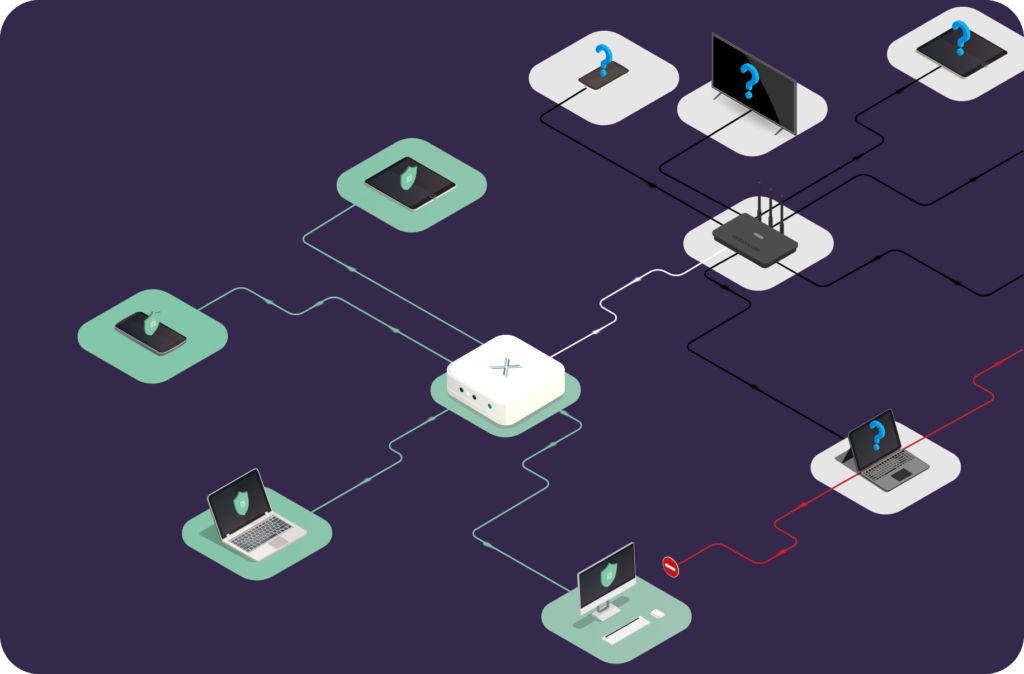
The Risk at the Edge: What Retailers Often Miss
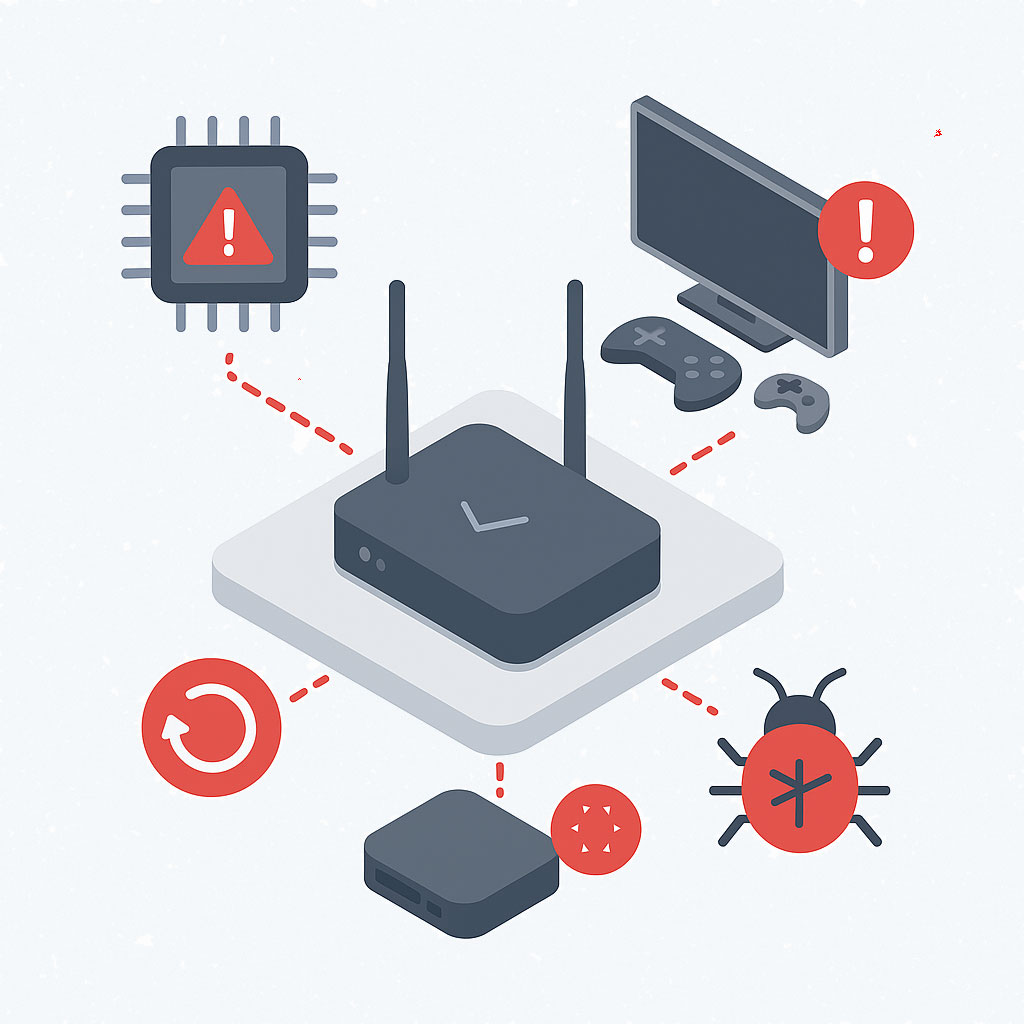
The uncontrolled network edge includes any device or network used to access your systems that sits outside your organisation’s direct control. Common vulnerabilities include:
- Default firmware with known weaknesses
- Unpatched routers, often running outdated software libraries
- Factory reset options that eliminate hardening efforts
- Shared Wi-Fi networks, with no segmentation between devices
- No visibility or logs, making investigations difficult post-incident
Both the UK’s National Cyber Security Centre (NCSC) and the EU Agency for Cybersecurity (ENISA) advise strong controls for firmware, network separation, and automated updates, all features built into Loxada’s platform.
Why the Threat Is Increasing
Retailers now face a more agile and decentralised form of cyber crime. Attackers no longer need deep technical skills. Thanks to the rise of Hacking-as-a-Service platforms and AI-powered exploitation tools, even non-technical criminals can:
- Scan for vulnerable routers used by remote staff
- Buy exploit kits that target specific retail technologies
- Use AI to generate targeted phishing attacks or manipulate DNS
- Move laterally once inside home or shared networks
- Exfiltrate customer data or disrupt internal operations with minimal effort
In this landscape, securing endpoints and cloud accounts isn’t enough. The network path between your people and your systems must also be secured.


Loxada: Practical Protection at the Network Edge
Loxada addresses this problem by creating a known, controlled connection point, no matter where your teams are located. Our platform replaces unreliable home or shared routers with secure, managed devices that:
- Run Loxada’s custom firmware, purpose-built for security
- Establish an always-on encrypted VPN tunnel
- Prevent lateral movement through network isolation
- Block malicious domains and filter threats before they reach endpoints
- Auto-update securely, without user involvement
- Resist tampering, even after a factory reset
No training. No configuration required. Just a trusted connection your teams can rely on, every time they log in.
Built for Modern Retail Operations
Loxada is designed to support a wide range of retail environments, including:
- Finance, HR, and procurement teams working remotely
- Regional and franchise managers accessing central systems
- Supply chain and logistics partners who work off-site
- Third-party vendors or auditors requiring temporary system access
- Hybrid staff or field teams operating in serviced offices or shared spaces
Whether it’s a payroll portal, supply chain dashboard, or internal compliance tool, Loxada protects how your teams access it.


Supports Compliance with UK and EU Standards
Retailers must now demonstrate resilience not just at the payment layer, but across the full data lifecycle, especially when sensitive or personal data is accessed remotely.
Loxada helps support compliance with:
- UK GDPR and EU GDPR obligations for secure data access and processing
- NCSC guidance on firmware, segmentation, and edge device management
- ENISA recommendations on securing distributed infrastructure
- DORA (Digital Operational Resilience Act) for retailers involved in financial services or embedded payments
- NIS2 Directive, which expands critical infrastructure requirements to include large-scale digital service providers
- PCI DSS best practices, particularly those relating to network segmentation and secure remote access
By addressing risks at the uncontrolled network edge, Loxada helps your organisation meet both regulatory expectations and internal governance goals.
Why Retailers Choose Loxada
- Protects operational and back-office access, wherever work happens
- Reduces reliance on user behaviour, by controlling the network layer
- Strengthens audit and compliance posture, with visible protections
- Requires no specialised skills or local configuration required
- Demonstrates proactive security to insurers and clients
- Deploys in minutes, with zero-touch rollout for regional or hybrid teams