
Financial Services
In the financial sector, your ability to operate securely and meet compliance obligations depends on more than just encrypted software or secure datacentres. It now includes how and where your team connects.
Whether it’s client data, transaction records, or regulatory reports, that data is increasingly accessed from outside your physical offices. As hybrid working continues, staff frequently work from home, travel abroad, or access systems from serviced offices and third-party spaces.
Each of these locations introduces risk at the uncontrolled network edge, the point where your systems meet infrastructure you don’t own or control.
The EU Digital Operational Resilience Act (DORA) now requires firms to assess and address ICT risks across their entire digital footprint, including remote access environments. Loxada helps you meet this obligation by securing the uncontrolled network edge.
Why Network Edge Risk Now Falls Within Scope
Even if your organisation uses secure platforms, multi-factor authentication, or encrypted tunnels, you may still be exposed if the underlying connection is insecure.
Most off-the-shelf routers:
- Ship with unpatched vulnerabilities
- Can be reset to insecure defaults
- Provide no isolation between devices on the same network
- Cannot be monitored or updated centrally by your IT team
These are not edge cases. They are the default setup in many home offices, temporary workspaces, and hotels.
Under DORA, you are now expected to identify, monitor, and manage third-party and ICT-related risks, including those introduced through remote or hybrid access. That means securing more than your application layer. It means controlling the physical and firmware-level infrastructure used to connect.

A Growing Threat Surface Across the EU
The European Central Bank and ENISA have repeatedly warned that financial entities are prime targets for cybercriminals and state-aligned actors. Attackers no longer require in-depth skills; instead, they utilise Hacking-as-a-Service (HaaS) platforms and AI-enhanced tools to rapidly scale up threats.
Loxada protects against common attacks that exploit network edge weaknesses:
- DNS hijacking and traffic interception before a VPN activates
- Man-in-the-middle attacks on shared or hotel networks
- Compromised routers used to eavesdrop or pivot into secure systems
- Lateral movement between devices on insecure local networks
These risks bypass traditional controls and remain invisible to your security stack unless you control the edge.
DORA and related guidance from EU regulators now place direct emphasis on ICT resilience, continuous monitoring, and secure remote access controls. If your team is connecting from unknown or unmanaged infrastructure, this may create a compliance gap.
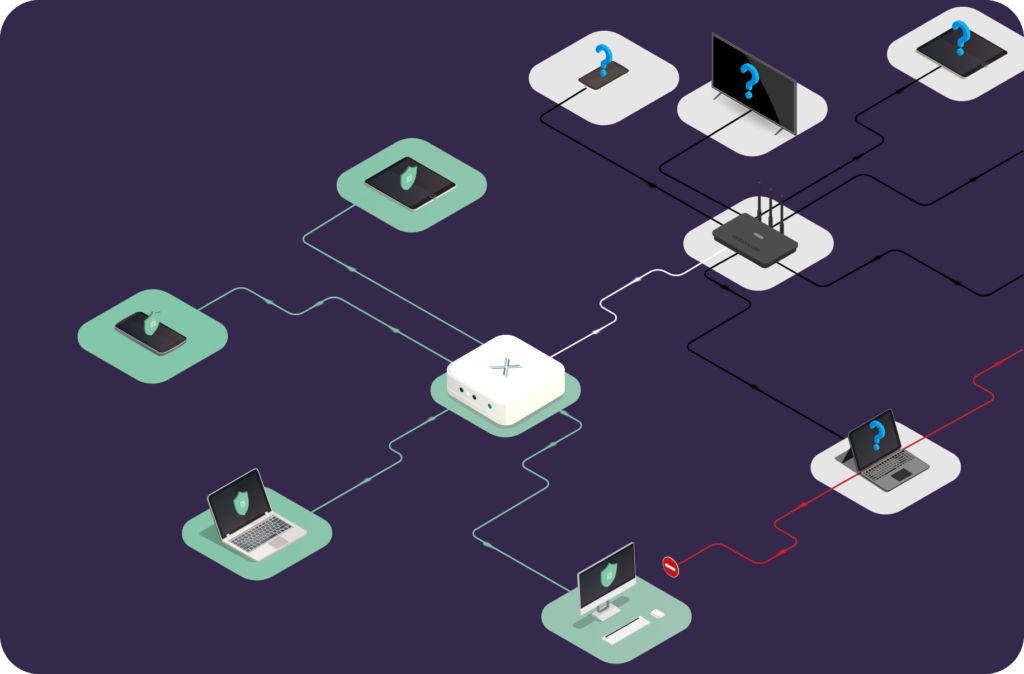
Loxada: Secure and Compliant Connectivity at the Edge
Loxada replaces untrusted routers with centrally managed, pre-configured devices designed for use in regulated environments.
Each device:
- Runs Loxada’s proprietary secure firmware
- Maintains a permanent VPN connection to a trusted endpoint
- Applies automatic security updates, verified and signed
- Blocks access to malicious domains and known threat sources
- Prevents rollback to an insecure state, even after a factory reset
No user configuration is needed. There’s nothing to install. The devices simply plug in and work, while maintaining a hardened, auditable security baseline.


Designed for Regulated Financial Workflows
Loxada helps financial services firms operating under DORA, EBA ICT guidelines, and other European regulatory frameworks meet the demand for secure remote operations.
Our routers allow you to:
- Demonstrate compliance with DORA Article 9 and related risk management obligations
- Extend security controls to home offices, mobile workers, and international teams
- Reduce risk from third-party infrastructure used during travel or offsite work
- Establish consistent protections, regardless of where your staff operate
We act as a force multiplier for your IT and compliance teams, turning a known blind spot into a controlled, visible asset.
Common Deployment Scenarios
- Private bankers working from home or travelling between client locations
- Risk or compliance staff reviewing confidential material from serviced offices
- M&A teams or analysts conducting due diligence in external environments
- Crisis response or DR teams needing secure connectivity in unfamiliar locations
- Contractors or consultants granted access to sensitive internal systems
Loxada gives you back control over the network edge, regardless of the setting, eliminating a critical DORA compliance gap without introducing operational complexity.

Why Financial Services Firms Choose Loxada
- Aligns with DORA’s emphasis on ICT resilience and access control
- Secures network edge devices previously outside your visibility
- Enables auditability and incident response under EU supervisory expectations
- Deploys at scale with no user training or software installation required
- Reduces the risk of non-compliance and operational disruption
Loxada allows you to extend trust to wherever work happens, protecting sensitive workflows without slowing them down.