
Retailers
Retail cybersecurity typically focusses on payment systems and customer-facing infrastructure.
But is your biggest risk hiding elsewhere?
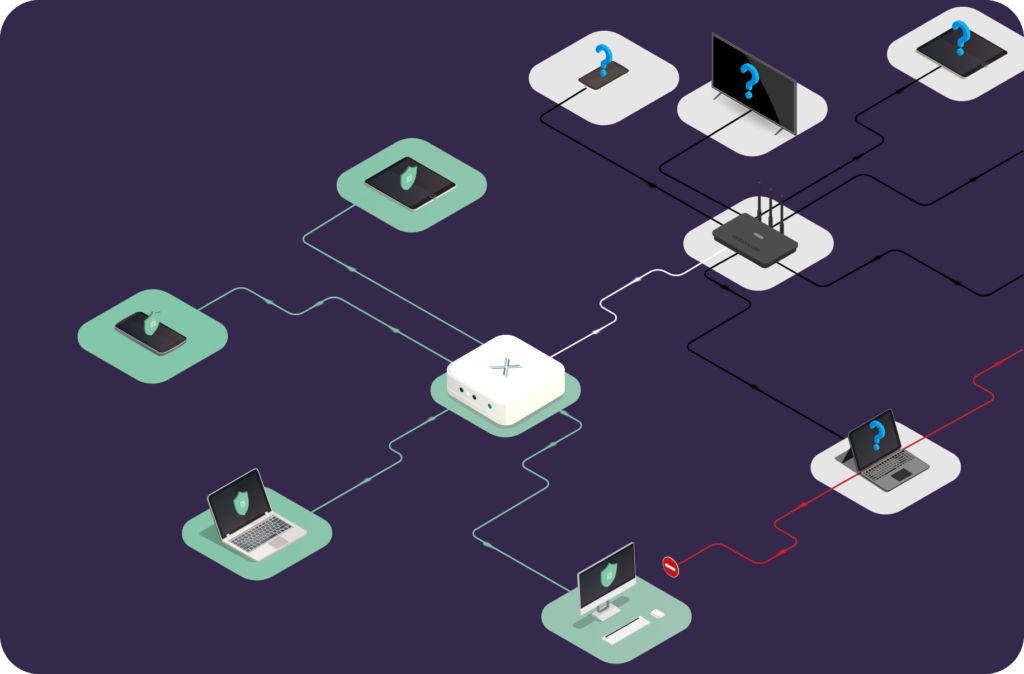
Behind every transaction is a quieter, riskier layer: operational and administrative teams managing inventory, logistics, HR, finance, and vendor systems.
Increasingly, these functions occur outside company IT; at home, in distribution hubs, or leased spaces with unknown networks.
That’s where the risk lies. When critical backend systems are accessed from uncontrolled network edges, your data, and business continuity, are exposed.
The Retail Attack Surface Has Grown
Many retailers believe their digital perimeter is secure. In reality, overlooked back-of-house access points now pose the greatest threat:
- Inventory staff logging into vendor platforms from home
- Regional managers uploading reports over hotel Wi-Fi
- Finance or HR teams working from shared office spaces
- Contractors using their own internet connections for systems access
These risks aren’t solved by POS firewalls or e-commerce monitoring. The weak point isn’t the application or your company network, it’s the user’s connection.

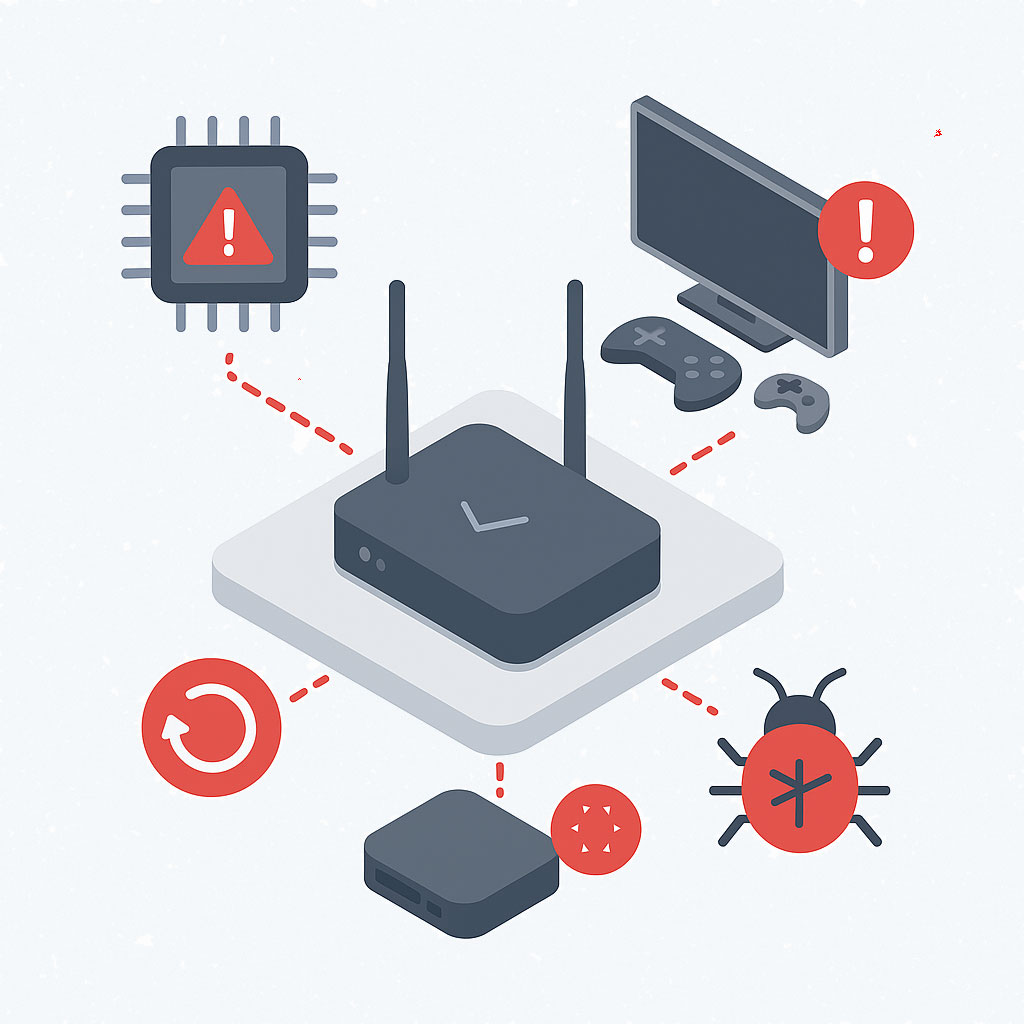
The Uncontrolled Network Edge: What Often Gets Missed
Unlike corporate-managed offices, these dispersed environments use off-the-shelf routers that are often:
- Running outdated firmware
- Using default settings, vulnerable to attack
- Shared with insecure devices (printers, smart TVs, gaming consoles, etc.)
- Completely invisible to your central IT team
Even diligent users are rarely able to keep their routers secure in the face of rapidly evolving threats. Many firmware updates only patch surface-level issues, leaving widely exploited third-party software libraries untouched, and retailers exposed to attacks.
NSA and CISA guidance on securing network edge devices warns against this setup. Their recommendations, secure boot, signed firmware, isolated networking, and update automation, form the foundation of the Loxada platform.
Why the Threat Is Growing
Attacking routers once required deep skill. Now, Hacking-as-a-Service and AI tools lower the bar:
- Cybercriminals can scan the internet for exposed routers with known vulnerabilities
- Exploits are packaged and sold like software, no skill needed
- AI can generate targeted phishing attacks to hijack sessions or DNS routes
- Lateral movement inside a home network is easier than ever
- Once inside, attackers can exfiltrate sensitive data or disrupt operations
These are not isolated, rare incidents. They’re an urgent, daily threat actively affecting the retail sector.


How Loxada Secures Retail Operations
Loxada is built to address this exact risk: the gap between a retail team’s endpoint and your central infrastructure.
We provide your distributed teams with a secure way to connect, every time, regardless of their location.
Our routers:
- Runs Loxada’s proprietary secure firmware
- Establish an always-on, encrypted VPN tunnel back to your organization
- Isolate connected corporate devices from other devices on the network
- Block malicious domains and known bad traffic by default
- Auto-update securely, with no user action or IT intervention required
No passwords. No configuration screens. No user training. Just a clean, trusted connection, every time.
Designed for Real-World Retail Workflows
Loxada supports retail organizations with:
- Admin or regional teams working from home or satellite locations
- Supply chain and logistics staff accessing vendor or ERP systems remotely
- Finance and HR teams dealing with sensitive internal data
- Franchise operators or field managers logging in from shared or public networks
- Third-party contractors needing temporary access under strict security controls
Whether your backend teams use Microsoft 365, ERP dashboards, inventory platforms, or payroll systems, Loxada ensures the data they access is protected at the point of connection.


Aligning with US Security and Regulatory Expectations
Aligning with US Security and Regulatory Expectations
Retailers are facing growing scrutiny from regulators, insurers, and supply chain partners, not just about what systems are secured, but how they’re accessed.
Loxada helps you demonstrate a responsible approach to remote security that aligns with:
- CISA and NSA guidance on securing the network edge
- FTC Safeguards Rules for retailers handling customer financial data
- PCI DSS best practices, particularly where edge device segmentation is required
- Cyber insurance evaluations, which increasingly assess router and firmware risks
- Retailer-vendor agreements that include security standards for data access
As cyber maturity advances, failing to secure backend access may soon be viewed as negligence, rather than oversight.
Why Retailers Choose Loxada
- Secures operational and administrative access across diverse environments
- Eliminates guesswork by controlling the network edge directly
- Works alongside your existing tools, doesn’t replace them
- Reduces the burden on your IT team by removing patching and configuration headaches
- Demonstrates a clear commitment to cybersecurity in client and audit discussions
- Deploys instantly, with zero-touch setup for users or contractors