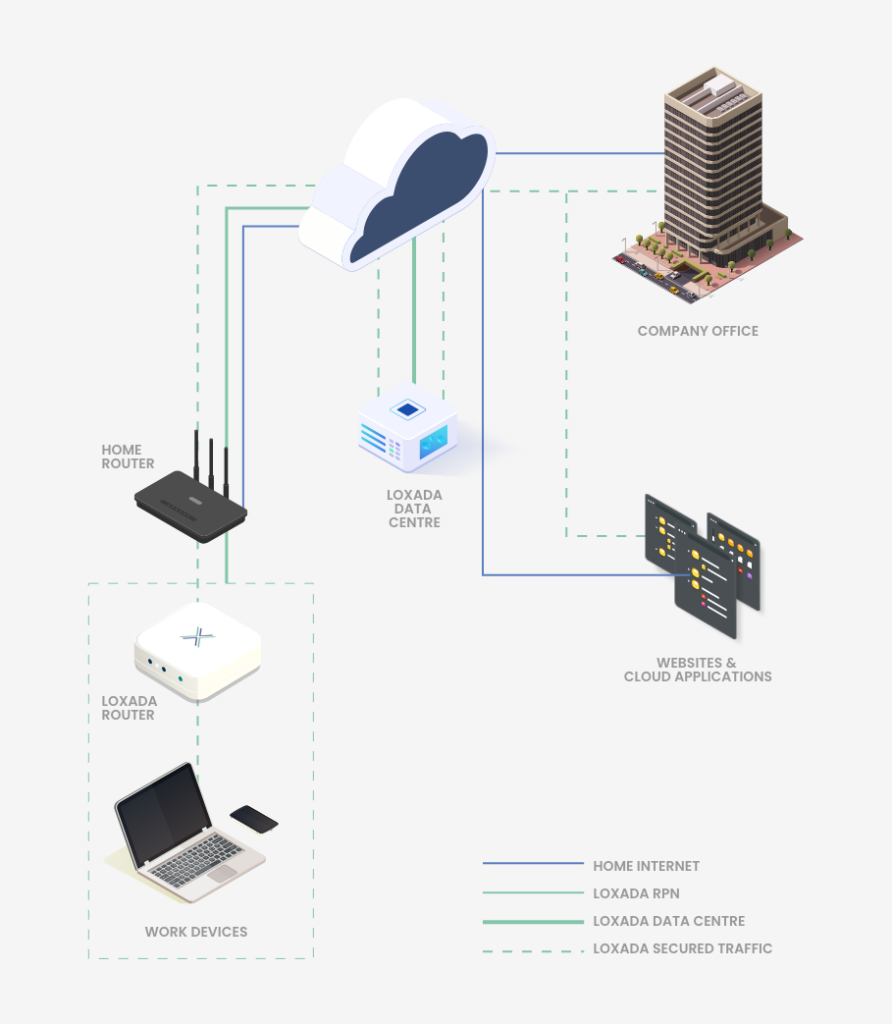
Not all routers are equal. And in locations outside your control, you often have no idea what kind of network your users are connecting through. Shared office spaces, client sites, serviced offices, coworking hubs, hotels, holiday rentals, even home networks all fall into the category of unmanaged infrastructure.
The issue? These environments can quickly become IT blind spots. You can’t patch what you can’t see, and you can’t harden what you don’t control. Even when users apply firmware updates, many of those updates still contain known vulnerabilities. And in most cases, there’s no visibility over whether updates are applied at all.
To quote the NSA, network edge devices “play a critical role in connecting external networks to internal resources and can be targeted by malicious actors to gain access or persist on networks.” The risk isn’t theoretical. It’s live, ongoing, and growing.
Source: NSA February 2025
In addition to firmware-level risk, there’s also lateral exposure. When your users connect to a shared or unknown network, you don’t know what else is on it. A compromised device elsewhere on that same Wi-Fi could scan or attempt to access your user’s machine. A compromised router could redirect traffic. Without control of the local network, your security posture depends on assumptions you can’t verify.